Cloud security posture management provides a means to continuously monitor the cloud environment, provide visibility, and identify and address vulnerabilities while predicting potential risks.
Securing a cloud environment today is difficult due to its dynamic nature and how it connects and disconnects to hundreds of networks and other resources. Lack of adequate visibility could lead to unnoticed misconfigurations and other security flaws that attackers can exploit and gain unauthorized access to the infrastructure.
Usually, incorrect and insecure configurations increase the attack surface, making it easier for criminals to attack. Eventually, this leads to the exposure of sensitive or confidential information, non-compliance fines, and financial and reputation losses, and other risks.
Ideally, a Cloud Security Posture Management (CSPM) deployment ensures that the cloud environment’s security aligns with best practices and set rules and expectations.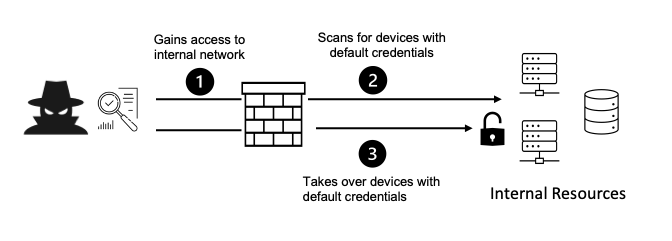
What Is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) is a set of tools and practices that enable organizations to assess the cloud and identify and resolve misconfigurations, compliance violations, and other security risks.
While some cloud service providers such as Amazon AWS, Google Cloud, Microsoft, and others have inbuilt CSPM capabilities, organizations on other platforms that do not offer these should consider third-party tools.
The solutions play a major role in cloud security by identifying, remediating, or alerting IT teams on security misconfigurations, risks, non-compliance and other vulnerabilities. Some tools provide automated detection and remediation of flaws.
Besides detecting and mitigating risks, a CSPM tool provides continuous monitoring and visibility into the organization’s cloud security posture. Additionally, some tools provide recommendations for hardening security.
Why Is Cloud Security Posture Management Important?
With the cloud comprising a wide range of different technologies and components, it becomes difficult for organizations to keep track of everything, especially if they do not have the right tools.
Any organization using cloud services should consider using a CSPM tool. In particular, this is essential for organizations with critical workloads, in highly regulated industries, and those with multiple cloud services accounts.
Benefits of using CSPM include:
- Performing continuous scanning and determining the security posture in real time.
- Allows an organization to gain continuous visibility across the entire cloud infrastructure.
- Automatic detection and remediation of misconfigurations and compliance issues
- Performing compliance benchmarking and audits to ensure that the organization is following best practices.
Despite the flexibility and productivity that the cloud infrastructure provides, it suffers from a wide range of security challenges, especially when misconfiguration and other bad practices increase the attack surface. To address these, organizations should deploy CSPM tools to provide visibility and identify and remediate the risks.
A typical CSPM tool will continuously monitor the cloud infrastructure and generate an alert whenever it detects an issue. Depending on the problem, the tool may remediate the risk automatically.
Otherwise, a prompt alert also allows the security, developers, or other teams to rectify the problem in good time. Additionally, a CSPM enables organizations to identify and address any gaps that may exist between the present and the desired states of their cloud environment.
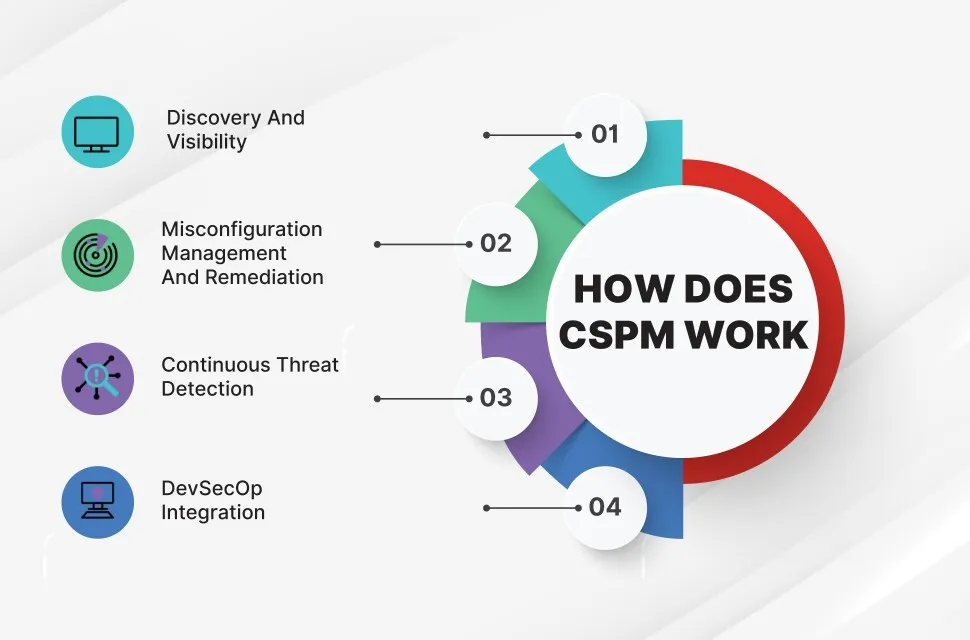
How Does CSPM Work?
A CSPM solution provides continuous monitoring and visualization of the cloud infrastructure to enable the discovery and classification of various cloud components and assess existing and potential risks.
Most tools compare active policies and configurations against a set baseline to identify drifts and risks. Further, some rule-based CSPM solutions work as per the set rules.
On the other hand, some solutions use machine learning to detect changes in the technologies and user behavior and then adjust how they compare.
A typical CSPM has the following main functions:
- Continuously monitor the cloud environment and services and provide complete visibility of the components and configurations.
- Benchmark the cloud configurations and policies against a set of acceptable guidelines.
- Detect misconfigurations and policy changes.
- Identify existing, new and potential threats.
- Correct misconfigurations based on pre-built rules and industry standards. This helps to reduce risks due to human errors that could result in incorrect configurations.
Although the CSPM helps to address a wide range of misconfiguration and compliance issues, they may differ in how they function. Some support automated remediation in real time.
However, automatic remediation may differ from one tool to another. Others support customized automation. Additionally, some are specific to certain cloud environments, such as Azure, AWS, or another service.
Some CSPM solutions provide automated and continuous monitoring, visibility, threat detection, and remediation. Depending on the solution, it may resolve the risks automatically, send alerts, and make recommendations and other functions.
What Is a Security Misconfiguration and Why Does It Occur?
Security misconfiguration is when the security controls are configured wrongly or left insecure, such as with default settings. This creates vulnerabilities, security gaps, and glitches that leave the networks, systems, and data exposed and at risk of various cyberattacks.
Misconfigurations occur mainly due to human error when teams fail to implement security settings correctly or not at all.
Typical bad practices include using the default settings, poor or no documentation of the configuration changes, granting excessive or risky permissions, incorrect settings by the service provider, and more.
It also occurs due to enabling unnecessary features, accounts, ports, services, and other components that increase the attack surface.
Other reasons why misconfigurations occur include the following:
- Displaying sensitive information on error messages
- Poor, weak, or lack of encryption
- Misconfigured security tools, unprotected platforms, directories, and files.
- Wrong hardware configurations, such as using default IP address, hardware and software credentials, and settings.
How to Implement CSPM in Your Organization?
A CSPM enables you to continuously assess your cloud environment and identify and address security gaps. However, implementing an effective CSPM solution requires proper planning, strategy, and time. Due to the different cloud environments and objectives, the process may differ from one organization to the other.
Besides the right tool choice, the teams should follow the best practices when implementing the solution. And there are several factors to consider.
Just like any other financial commitment, the security teams must define the objectives of the CSPM in addition to getting the approval of the senior management. Afterward, they should take the following steps.
- Define the objectives, such as the risks you want to detect and resolve. Additionally, identify and engage the relevant teams to oversee the deployment.
- Identify the right CSPM solution, and use the preconfigured or your custom rules to detect the misconfigurations and other vulnerabilities.
- Establish how to evaluate or assess the cloud environments.
- Continuously scan your cloud environment and assets to identify and address security risks, including those that changes in the cloud environment may introduce.
- Evaluate the results and establish the critical areas to prioritize the remediation. Some tools may help to assess the severity of the risks it detects and prioritize those to resolve first.
- Resolve detected risks automatically or manually. Also, you could configure the tool to notify relevant teams to take action.
- Regularly repeat the process and fine-tune it to address changes that could have occurred in the ever-evolving cloud environments.
How a CSPM Tool Provides Visibility of Cloud Infrastructure?
Most organizations may not know the number and types of their cloud resources, those running, and how their configurations. In most cases, the lack of visibility into their cloud environment may lead to running various services with several misconfigurations.
A typical CSPM tool continuously scans the cloud environment to provide visibility into the security posture. As it does this, it discovers the assets, services, and other cloud resources while assessing the security by checking for misconfigurations and other vulnerabilities.
Generally, the tool visualizes the assets and helps the organizations to discover and understand network interconnections, services, workloads, pathways to data, and other resources. This allows teams to identify misconfigurations, security vulnerabilities, unused assets, and services, as well as check the integrity of recently installed hardware or software systems, etc.
For example, the CSPM tool discovers cloud assets such as virtual machines, Amazon S3 buckets, and other resources. It then provides the visibility of the cloud environment, including its assets, security configurations, compliance, and risks. Also, the visibility allows the teams to find and address blind spots.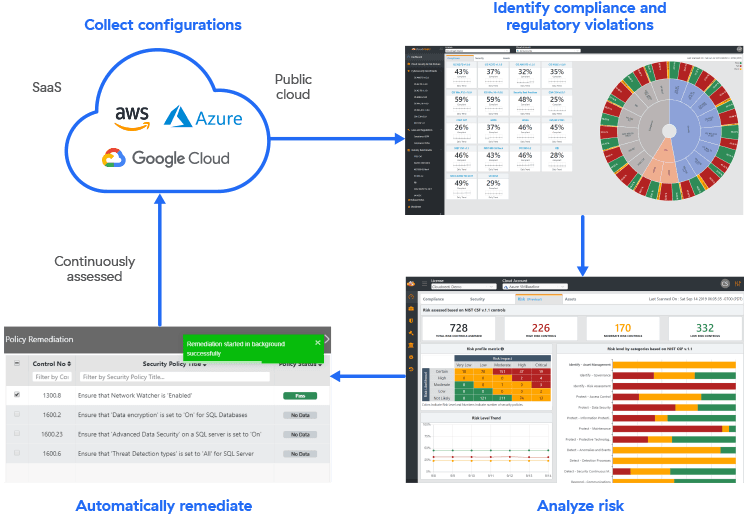
Challenges of Cloud Security Posture Management
Although the CAPM tools provide several security benefits, they also have various disadvantages. These include:
- Some CSPM tools without vulnerability scanning features rely on other solutions. And this can complicate the deployment and response.
- Lack of adequate skills to deploy and maintain the CSPM solution.
- Automatic remediation could result in problems. Generally, resolving problems automatically is faster and more efficient if done right. However, some issues may require manual intervention.
- In practice, most CSPM tools do not proactively stop ransomware, malware, and other attacks. Mitigating an attack may take several hours, which could mean more damage. Additionally, the tool may not detect threats propagating laterally across the cloud environment.
- Some CSPM functions are usually available as products of the cloud service provider or features of other cloud-based tools, such as cloud workload protection platform (CWPP) and Cloud Access Security Broker (CASB). Unfortunately, these cloud-first tools do not provide on-premise security.
Learning Resources
Below are some courses and books that will help you understand more about cloud security posture management and other practices
#1. Check Point Jump Start: CloudGuard Posture Management: Udemy
Check Point Jump Start: CloudGuard Posture Management is a free, simple, and informative online course offered by Udemy. You only need the same basic computer skills to understand the CSPM.
#2. Container Security & Cloud Security using AQUA – Udemy

The Container Security & Cloud Security using AQUA course will help you learn about container images, their security, and how to scan them with Aqua security solutions.
You will also learn how to detect misconfigurations in an AWS platform, about cloud security posture management, and how to implement it using the Aqua solution.
#3. Cloud Security Posture Management Complete Self-Assessment Guide
The book guides you on how to assess your security posture, visualize your cloud resources and determine who is using them. It also comes with digital tools that enable you to assess the security measures, policies, and other solutions in place.
| Preview | Product | Rating | |
|---|---|---|---|
 | Cloud Security Posture Management Complete Self-Assessment Guide | Buy on Amazon |
Further, you will look at past attacks and challenges your organization is going through to protect the workloads. Additionally, you will assess how secure is your applications and data, who has access to them, and who is authorized to take certain actions.
The CSPM self-assessment guide will help you establish your CSPM challenges and how to overcome them and protect your cloud environment.
#4. Cloud Security Technical Reference Architecture
The book provides reference architecture the CISA, OBD, and other security agencies recommend.
| Preview | Product | Rating | |
|---|---|---|---|
 | Cloud Security Technical Reference Architecture | Buy on Amazon |
It shows that organizations and agencies migrating their workloads to the cloud should protect their data collection and reporting using various tools, including the CSPM.
Final Words
The cloud infrastructure continuously changes, and organizations without adequate visibility may expose their environment to attacks. As such, it is essential to regularly audit the security settings, configurations, and controls to ensure compliance, even after adding a new component. The teams should then address any drift in the configuration as soon as possible.
One way of achieving this is by using a reliable cloud security posture management solution. The tool provides visibility that allows organizations to protect their cloud assets against non-compliance and misconfigurations, such as outdated security updates, incorrect permissions, unencrypted data, expired encryption keys, etc.
Next, check out how to find web server vulnerabilities with the Nikto scanner.

